Today’s world is always at the gun’s scope of cybercriminals. Every day, one will find innumerable headlines about small to big cyber attacks on an individual’s account, a firm, or sometimes even the multi-billion dollar organizations that have access to the highly complex prevention measures. We are experiencing it on a large scale. And that’s why data security has emerged as one of the top concerns of people as well as the government. As the internet has become stronger, data has become much more valuable than money.
Encryption technology helps to save your data and protects your devices, accounts, and crucial information from cyber attacks. Nowadays, it is hard to find an application without any form of encryption technology. If you are using whatsapp, you must know that it uses an end to end encryption method to keep your communication secure, another example of the digital platforms using encryption is Internet Banking. So, knowingly or unknowingly we all are using an encrypted network in our daily lives.
In the information age, where countless red eyes of hackers and data breaches are looming and lurking all over the internet, encryption technology lets us sleep peacefully on dark nights without worrying much about our personal data and information being stolen.
What is Encryption?
In simple words, encryption is a way to put a wall of secure code on our valuable data so hackers and breachers either won’t recognize it or won’t be able to decode it to its original form. It is majorly used to send data or information from one device/place to another and store it safely away from prying eyes. Storing & Transferring are two main use cases of cryptography. In simpler words, it is a technology in which your data is locked with a unique key and can only be unlocked by the person for whom it is actually sent or intended. Therefore, middlemen and breachers find their methods useless as they don’t have the key.
The use of cryptography began in the 19th century during World War II. This was the time when the German forces secured their day-to-day communication by cryptography ciphers. However, their code was broken by England force’s brilliant mind Mr. Alan Turning.
Ciphers are very complicated algorithms that are used during the encryption process. The way it’s processed is quite mundane as it is just about converting readable text into random characters so they don’t make any sense to middlemen if he succeeds in his breaching attempt. Therefore, despite being a simple technique, it is quite effective. The encryption can only be decrypted if the receiving party has the key. With the key, the receiving party can turn the unreadable text into a readable one once again.
Types of Encryption
A person or firm can take benefits from two kinds of encryptions today. The first is Private Key Encryption aka symmetric encryption. And another one is Public Key Encryption which is also known as asymmetric encryption.
Both of these encryption techniques are kind of similar as they work on the same principle i.e. encrypting the data at one end and decrypting it at the other end. And in the meanwhile hide it from any third pay in between. However, there is a slight difference in them when it comes to taking the steps needed in encrypting the data. They may have a slight difference in terms of how they work? But, that slight difference makes their use cases totally different from each other. For example, asymmetric can be used to validate the authenticity of the document as well but not the other one can do the same.
One important thing about them is “Either of the two keys – Public or Private can be used for encryption with another key used for decryption”. It all depends on what you are trying to achieve using this technology.
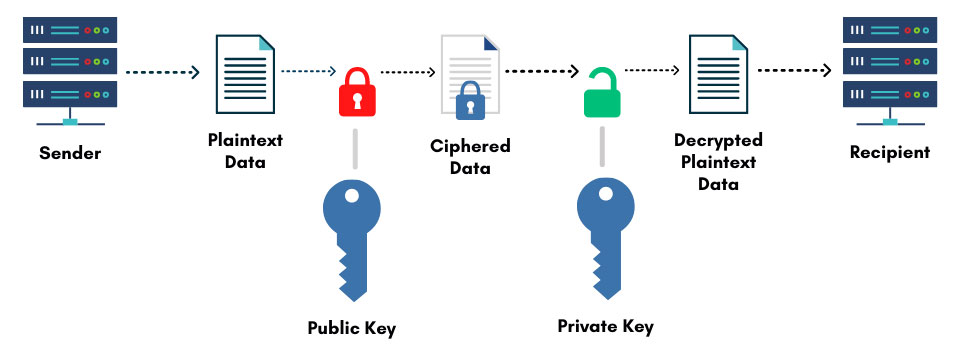
Public Key Encryption ( Asymmetric )
In this method, we use two kinds of keys. One of them is a mathematically matching private key and the second one is a recipient’s public key.
For example, if the purpose of using public-key cryptography is to keep the message secure then the process would go something like this;
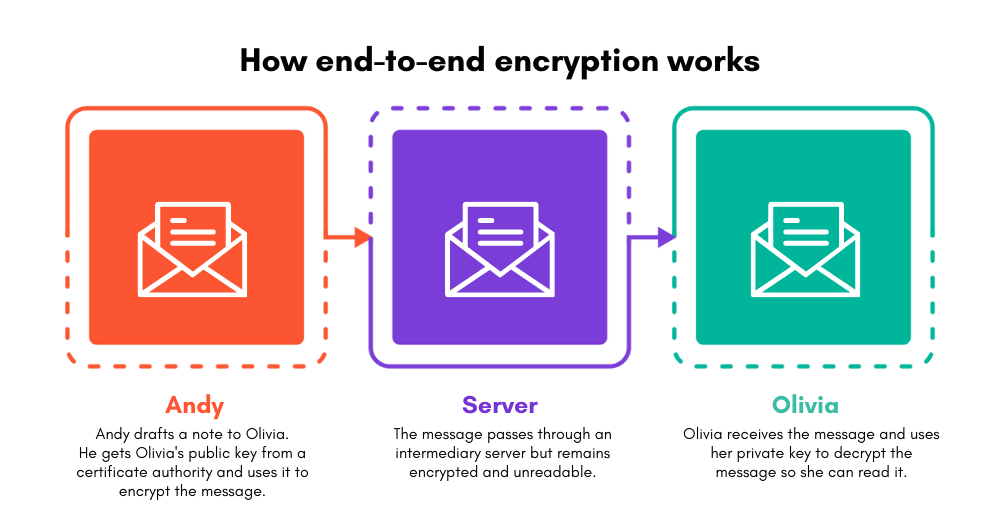
Andy and Olivia want to communicate with each other securely, so they decide to use Asymmetric Encryption.
Both Andy & Olivia generate their public/private key pairs and share their public keys with each other. It is important to generate and share the public keys because if you want to communicate with someone privately, you need to have their public keys to decode their message.
Andy’s message “I have planned a small surprise party for my wife’s birthday and you are invited”
Andy encrypts it using Olivia’s public key because he wants only Olivia to be able to read it and then send it to Olivia.
Andy’s wife wants to know what exactly he is planning for her birthday and tries to snoop the message but she just sees gibberish like “xlxlhsdfhsfl asdf shhh”.
Olivia receives the message in the gibberish form.
Lateron, Olivia uses his private key to “Decrypt the message”
Olivia gets the original message which was “I have planned a small surprise party for my wife’s birthday and you are invited”
In simple words we can say that, for encryption a public key is needed and for decryption a private key is needed. In some cases, another public key is also required for additional encryption.
Private Key Encryption ( Symmetric)
Private key encryption is called symmetric encryption for a solid reason. It is way different from its Public Key variant when it comes to key usage as It only needs one key for both encryption and decryption. In both of the two, keys are required and that’s a similarity. However, the major factor of consideration here is, the intention of usage is different. Sometimes the purpose of encryption is not to share the message or information with someone in an encrypted format but to store it safely somewhere with the owner.
For example, Andy has something which he wants to securely store in his PC and doesn’t want to share it with anyone. Here, the intention is not sharing, he just wants to keep it safe from prying eyes. In such a case, Andy would simply use symmetric encryption and keep his encryption key safely stored somewhere.
Technology Used in Modern-Day Encryption
Over the years, the latest technologies have replaced the old ones and the globe has shifted to an advanced age of information. Following that, the methods used in encryption have shifted to their high-tech, more complex versions as well. Today’s advanced encryption processes use comparatively larger key sizes. That helps in concealing important data. The bigger size of keys further helps in vastly increasing the number of combinations to decrypt the information while the authentic receiving end would know the exact decrypting keys.
Brute force attacks nearly become ineffective as the encryption algorithm has been substantially improved and its size has been thoughtfully expanded. To break such a kind of encryption, brute force attacks would need to have a huge amount of time, effort, and resources. If we take an example of 40-bit encryption and 64-bit encryption. The difference of just 24 looks very minimal to us. However, on the real grounds, it will take 300 times more time, effort, and resources to break it in comparison to 40-bit encryption. We are not talking about the 128 and 256-bit encryption that many modern algorithms work on. There are trillions of possible combinations a hacker has to attempt in order to break such a combination.
• 3DES (Data Encryption Standard) : Refers to the Data Encryption Standard and a type of private key (symmetric key) encryption.
• AES (Advanced Encryption Standard): Used to encrypt and decrypt the data.
• RSA (Rivest-Shamir-Adleman): It is not a symmetric encryption and works as a public key (asymmetric) method.
Uses of Encryption
Encryption is used in several different ways but with the same aim to build a solid foundation for data security. Let’s have a look at the topmost uses of encryption:
End-to-End Encryption
When the data is transferred from one source to another, a secure connection is needed. Otherwise, a weak connection will indicate a green flag to hackers and the middlemen altogether. End-to-end encryption is the process in which such a secure connection is achieved.
Securing data on the users’ devices, End-to-end encryption decrypts the data only when the recipients receive it on their respective devices. It means the shared data is end-to-end encrypted and can neither be decrypted on the server nor in the transit and also not on the user’s device. With utilizing the public key encryption approach, the used cryptographic keys to encrypt and decrypt the data are stored on the endpoints.
In end-to-end encryption, the data gets encrypted on the sender’s device and prevents third parties and even ISPs from reading it until it reaches the receiver’s device. The best examples of end-to-end encryption are Whatsapp, Zoom, and Facebook.
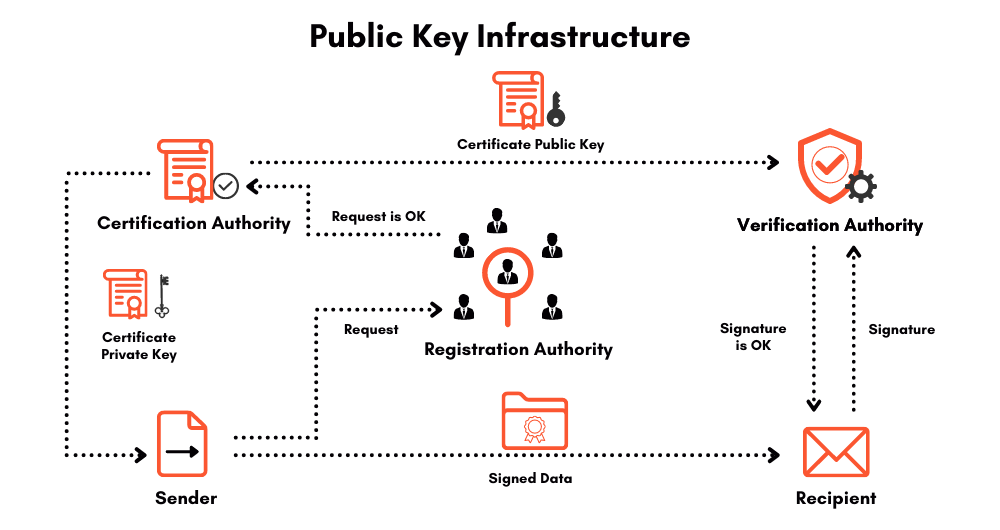
Digital Signatures
Digital signatures are a type of electronic signature. They are used to securely sign an electronic document in the form of a coded message. A digital signature is basically used to assign a signer with a document in a recorded transaction. The format they used is called PKI (Public Key Infrastructure) which is an encryption framework that protects the data and secure end-to-end communications by creating unique digital user identities.
Using digital certificates for PKI authentication is among the most effective ways to protect sensitive data. The best part about it is the integrity of the associated Certificate Authority and Registration Authority which provides incredibly elaborated and unique digital certificates to every user. Certification and registration authorities make it nearly impossible to decrypt the data without verification authority on the recipient’s device.
HTTPS
We have all heard about HTTPS in our engineering colleges or during our job. It is actually a secure version of HTTP (hypertext transfer protocol) known as HTTPS (hypertext transfer protocol secure). It is used when we send data from our browser to a website or vice versa. Securing data that a user often sends or receives on the internet very frequently is important, such as bank login details and email accounts’ credentials.
Therefore, securing them is essential. HTTPS improves the three important aspects of internet data transfer – Confidentiality, Integrity, and Authenticity. When a website is SSL certified It has HTTPS appearing in its URL which means the communication protocol is encrypted with TLS – Transport Layer Security. TLS is an advanced version of Secure Sockets Layer with more security.
SSL/TLS includes a set of steps through which two systems – user and site verify each other and communicate through the secure SSL/TLS tunnel. It enables both the servers to verify each other’s identities while using a cipher suite and TLS version in communication, establishing the session keys and securing the communication through symmetric encryption.
Let’s understand it with an example:
Client: Hi, I wish to securely communicate with you. Please find my cipher suite and SSL/TLS version.
Server: Hi, Thank you for sharing your cipher suite and SSL/TLS version, I have checked them and we’re good to move forward. Please find my certificate file and public key for the verification.
Client: Your certificate has been verified, It seems good to go, but let me also verify your private key. To do so, I am generating and encrypting a secret session key using the public key you have provided. You can then decrypt it with your private key and we will be asked the session key to encrypt and decrypt the information.
Server: Sure
Note – Now both of them know whom they’re talking to and their communication is also secured with the secret session key / master-key.
Client: I have sent you a test message to check that the session key is working or not, once you receive it please send me the decrypted version of the received message. If everything goes well, our data is secured.
Server: Yes, it is working. We can securely communicate with each other now.
Certificate
Certificates include a public key on which a label is attached. It is used to identify the owner. Thanks to the certificate, the data you send on the server can’t be read by anyone else other than the person you sent it to. For example, every HTTPS requires a TLS or SSL certificate to install on your server. The TLS or SSL certificate stores the Private and Public Keys you generate randomly. Once generated, the private key helps decryption on the receiver’s end while the public key verifies the receiver.
Certificate Authority
The digital certificates we talked about earlier are often issued by Certificate Authority (CA). When a user visits a website using HTTPS, the ownership verification process is done. And, that happens because the owner has used a Certificate Authority (CA) to prove his ownership over the website. The process works by – When you visit a website, the CA signs the certificate and sends it to your machine, then your machine checks and validates whether the certificate is legitimate or not, if it’s legitimate, the data is added to the trusted authorities list.