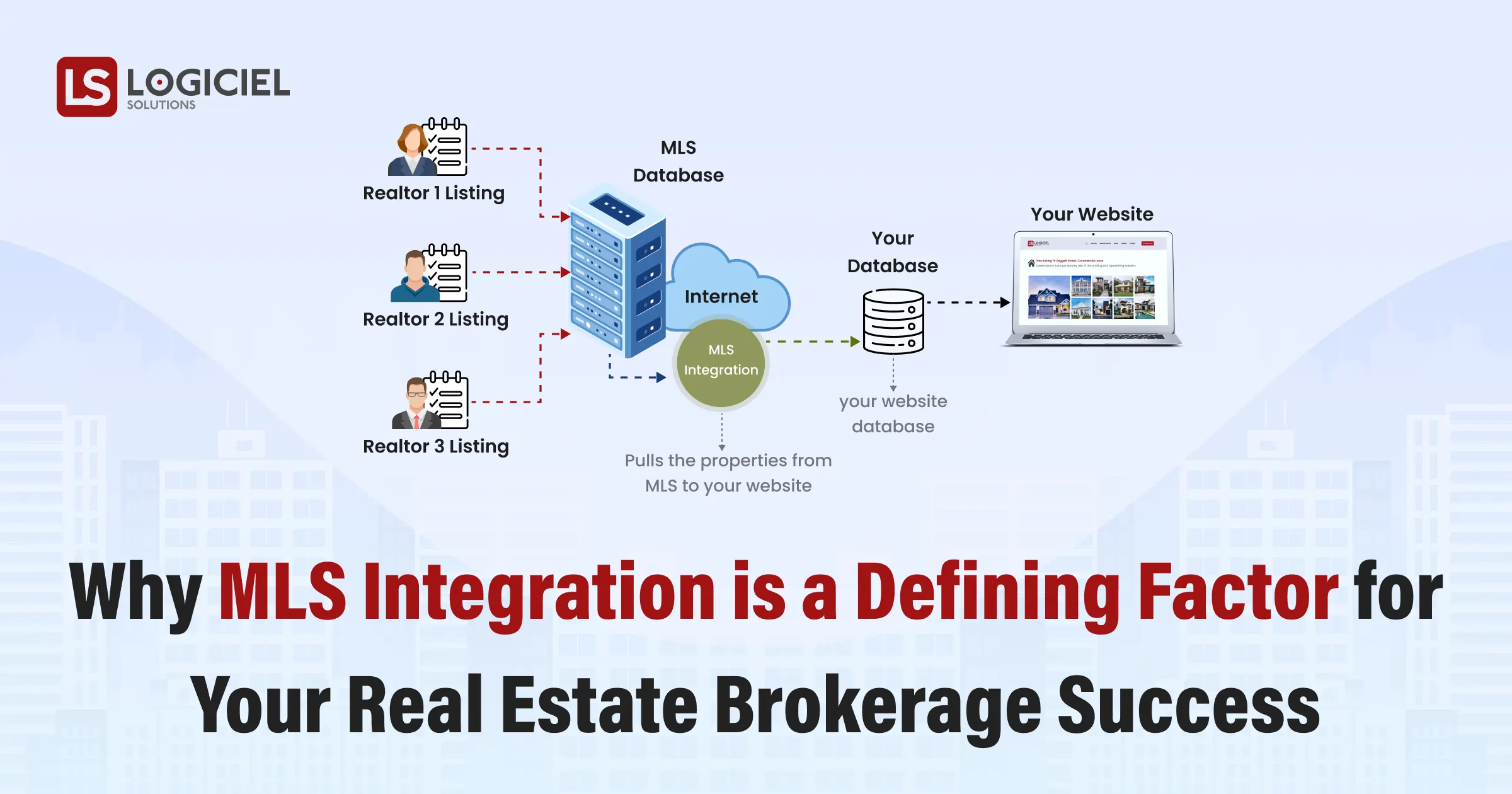
Real estate is no more just about buying, selling or renting properties. In today’s modern digital era of real estate, it is more about serving a personalized experience to the customers.
It is about creating meaningful interactions with customers through technologies like virtual tours and predictive analysis. It is also about boosting productivity and operational efficiency with automated workflows, smart contracts and multiple CRM systems.
While the real estate industry is gaining the momentum to embrace technological advancement to reshape the way they do business and cater their customers’ needs, it is also becoming vulnerable to cyber attacks with bringing an immense amount of sensitive data online.
Addressing cybersecurity challenges is critical for the realtors in order to safeguard their data and build strong and reliable customer relationships. Realtors must level up their data security standards implementing the robust protocols.
In this article, we will walk you through to the top cybersecurity threats and best practices to avoid them.
Let’s get started with understanding Why do cyber criminals target real estate organizations?
Real Estate cyberattacks may not sound very prominent at first glance but, there are various surveys that show the real estate industry is no more immune to the cyber incidents and a serious data leak could lead a company to sink and even lose its brand reputation for always.
So, why would the hackers target Real Estate?
Ever since the Real estate sector has started their digital transformation journey and made their processes digital including transaction and financial management, they have been a lucrative target for the cyber criminals to commit frauds.
The Top 3 Cybersecurity Threats in Real Estate
There are several different ways a hacker can attack real estate companies such as:

1. Phishing
As per the surveys the approximate number of daily sent phishing emails by cyber criminals is 3.4 billion. In this scam, hackers mostly send emails or text messages with tempting deals and schemes to lure realtors to click a link or download an attachment. Phishing is quite a popular approach for the cyber criminals to scam the real estate professionals, brokers and agents.
The reason behind this popularity is they know that being a real estate professional you get dozens of emails on a daily basis and it’s more likely that you would mistakenly click on the links or download the sent attachment and would fall in their trap unknowingly.
2. Ransomware
This is the most common type of malware used to take unauthorized access or control of a company’s server to encrypt their data. The hackers first find the gaps in the company’s cybersecurity framework and then get their attachment containing ransomware downloaded to infect the entire network of the targeted company.
Once they gain the access, they freeze all the data and make all the files unusable for the attacked company. They then ask a huge amount of ransom to release the data. In most cases the company who is the victim of Ransomware has to pay the asked amount in order to save their valuable data and brand reputation.
3. BEC (Business Email Compromise)
BEC scams are significantly growing in the Real estate industry. Recently one of the Internet crime reports by the FBI highlighted that In 2020 approx 13,638 people were scammed by BEC in real estate. It was also stated that the BEC scam was ranked No. 7 out of over 30 types of scams reported.
We have just learnt how serious this scam is in the Real Estate industry now let’s see how it works?
So, it starts with a BEC scam victim who is usually the buyers’ agents receiving an email about the soft offer that has just come in on the behalf of the seller’s real estate agent. It states that the deal is valid just for now and if they don’t close it now by paying the token amount, they will lose the deal. And when the payment is made, it gets routed to the imposter bank account.
Best Practices and Solutions to Enhance Cybersecurity in Real Estate
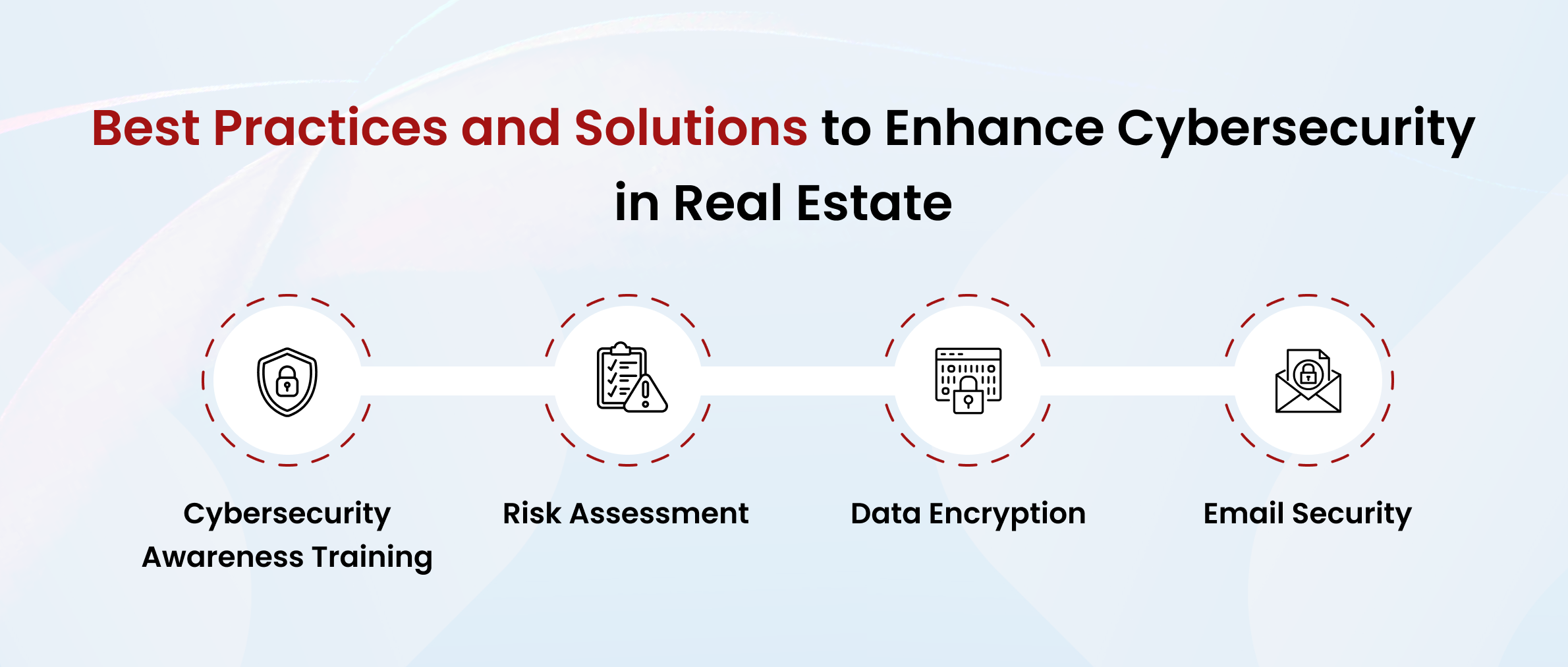
1. Cybersecurity Awareness Training
As we have read above cyber threats often succeed due to employee mistakes or negligence like clicking on the fraud links or downloading infected attachments.
Conducting regular cybersecurity training sessions is the very first step towards strengthening your organization’s cybersecurity. It will keep your employees updated about the ongoing cyber security threats and enable them to respond to them effectively.
2. Risk Assessment
Another important step to safeguard your organization’s sensitive data is to regularly conduct thorough risk assessment.
Keep a keen eye on your company’s network and systems. Don’t forget to update or renew your software and antivirus programs on a timely basis to find out potential security gaps and vulnerabilities.
3. Data Encryption
Having your data encrypted means you have an extra layer of security to safeguard your sensitive information. These encryption protocols help you keep your data safe with a highly secure key.
It means if in case the hackers get access to your data, they still won’t be able to view, use or steal any of the information without decoding that with the encryption key.
4. Email Security
Since emails are the most common form of cyber threats in Real Estate, it is highly recommended to secure them with TTBS’ email security.
This is one of the best solutions to safeguard all real estate accounts configured on your company’s server against various serious threats such as phishing and spoofing attacks. Another best part about this solution is it automatically eliminates the spam emails where most of the scam emails land.
Final Words
While transactions and client engagements are moving online, safeguarding this huge amount of sensitive data, financial records, and transaction details have become a major concern for real estate professionals.
Due to this shift realty firms are now encountering hurdles more than ever before in securing their customers’ sensitive information. Staying updated about the real estate cyber threats and effectively implementing the best practices, they can protect their sensitive data.